Create a Webhook
You can create webhooks following two paths:- From Adaline’s main page click on Settings. Under each project you will see a Webhooks section:
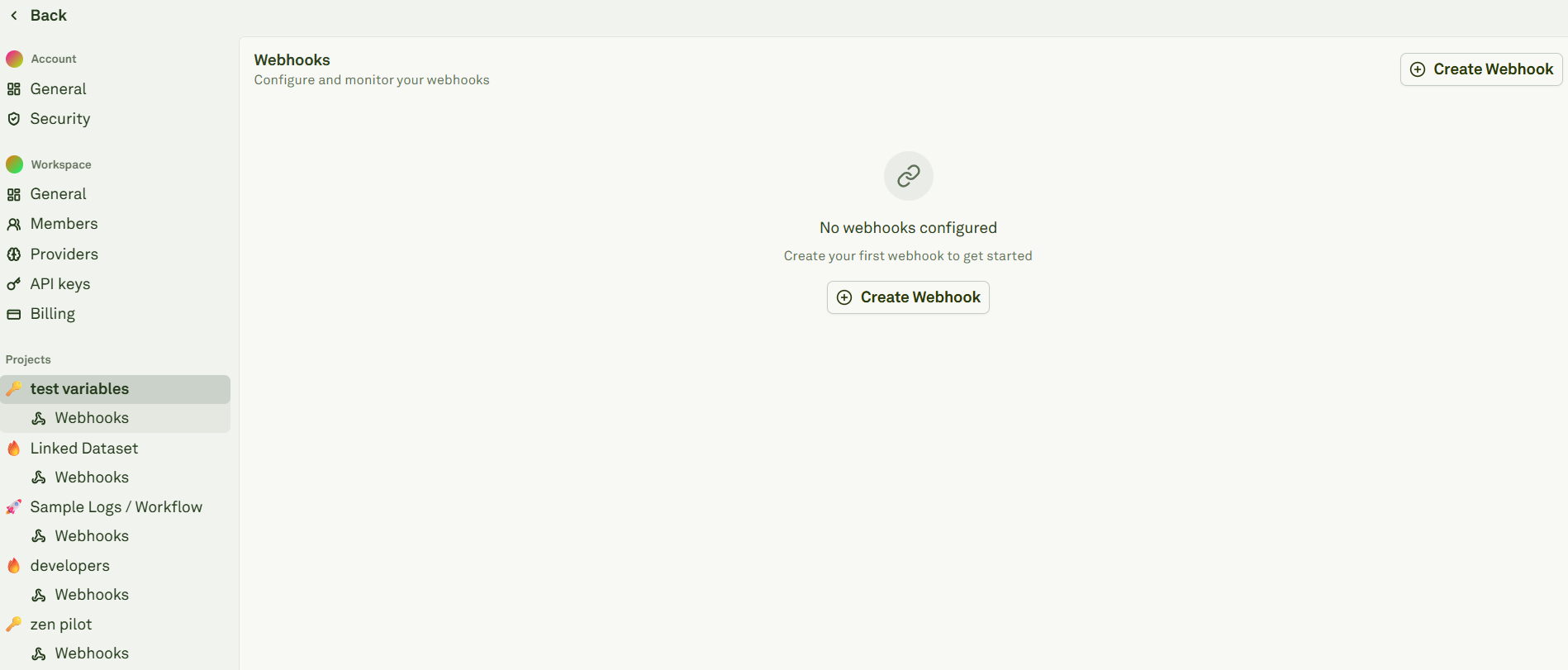
- From an undeployed project:
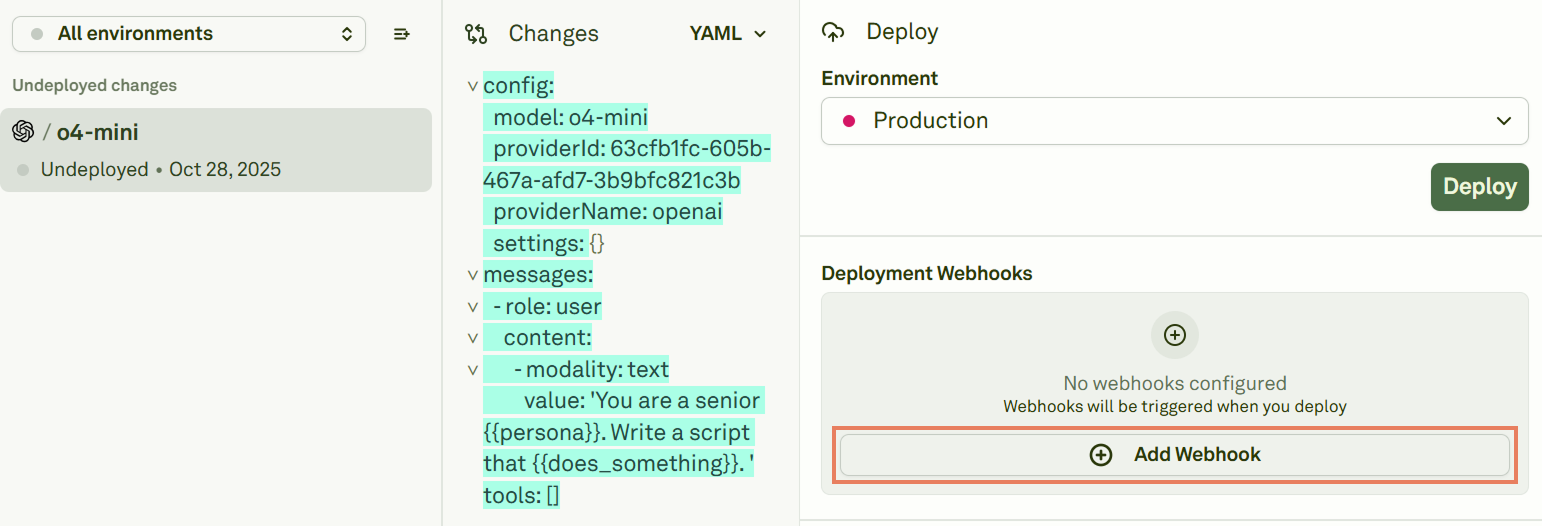
Configure a Webhook
When creating a new webhook, Adaline will provide you with the following space: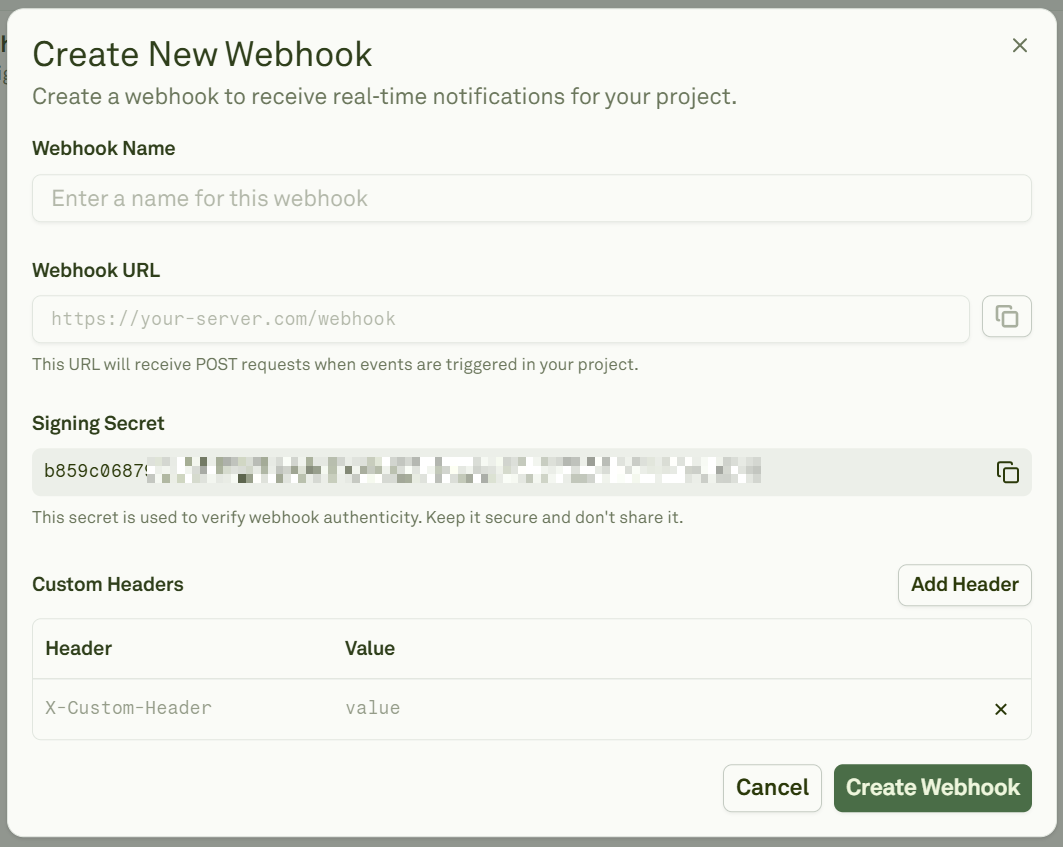
- Webhook Name: A short name for your destination.
- Webhook URL: The HTTPS endpoint to receive event.
- Signing Secret: Adaline generates this for you. Copy and store it securely.
- Custom Headers: Add custom headers your endpoint expects. Webhooks automatically subscribe to the create-deployment event.
create-deployment. This event is fired whenever a new deployment snapshot is created for a prompt bench and environment. Below is how a payload for this event should look like:
- Method: POST (JSON body)
- Content-Type: application/json
- Signature header: X-Webhook-Signature
X-Webhook-Signature header. The value contains a timestamp and one or more signatures to support secret rotation.
Below is the header format:
Verify Signatures
Below is a concise TypeScript example that parses the signature header and verifies it against your signing secret:- raw_body: The exact request body string.
- header: The
X-Webhook-Signaturevalue. - secret: Your signing secret.
Test Webhooks
From the webhook details page, click “Send Test Event” to confirm connectivity and signature validation: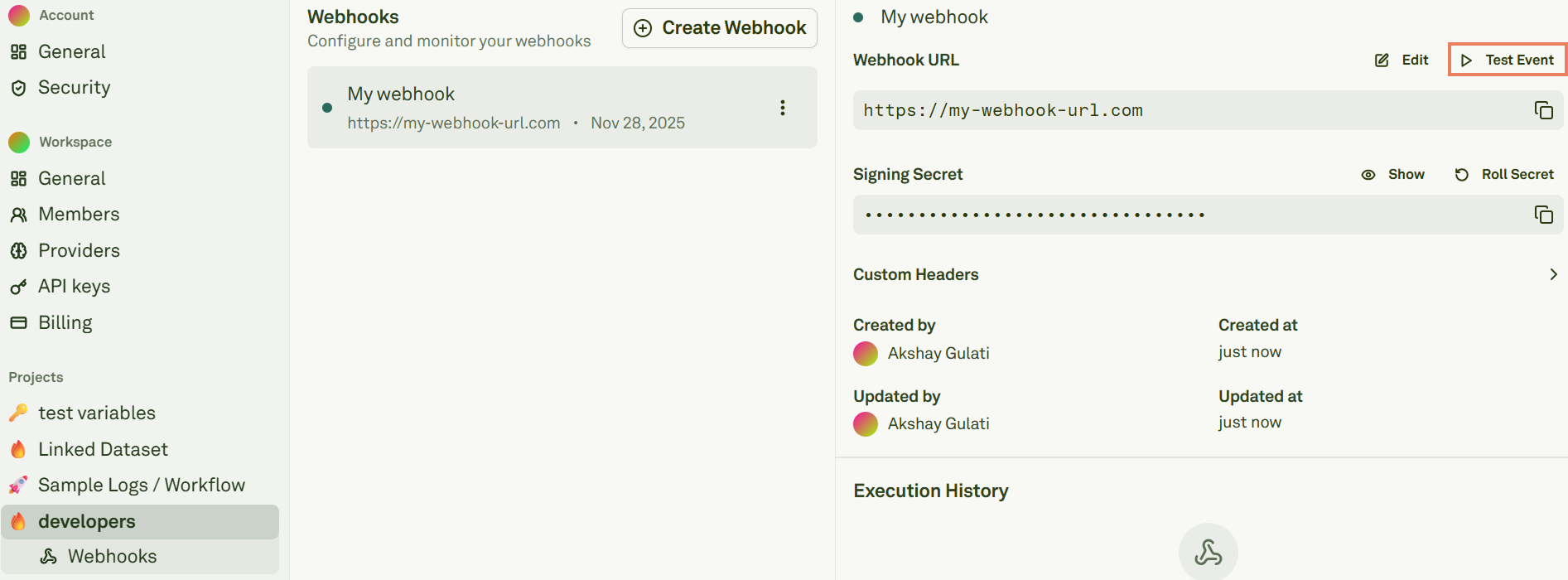
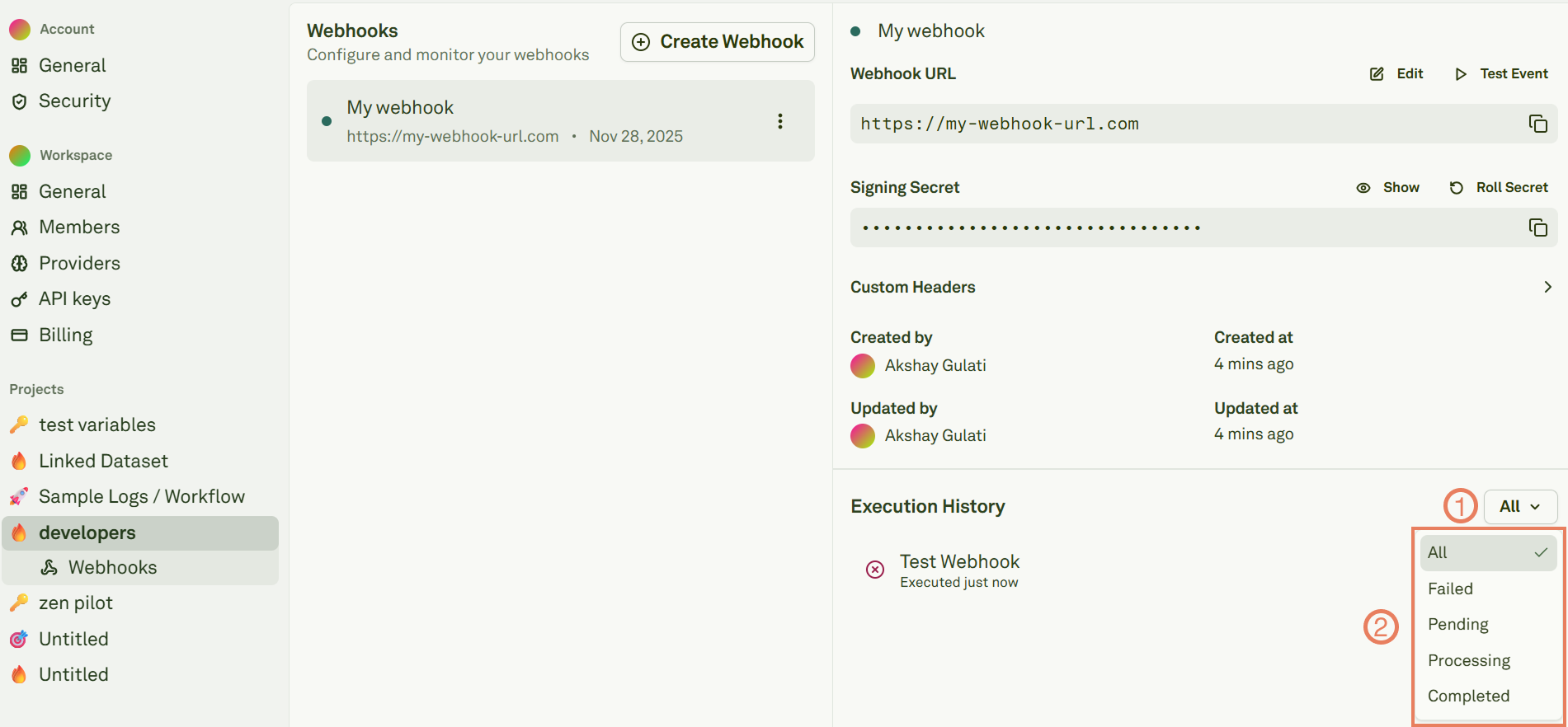
200 OK after verifying the signature.
Roll Secrets
Roll the signing secret from the Webhook details page: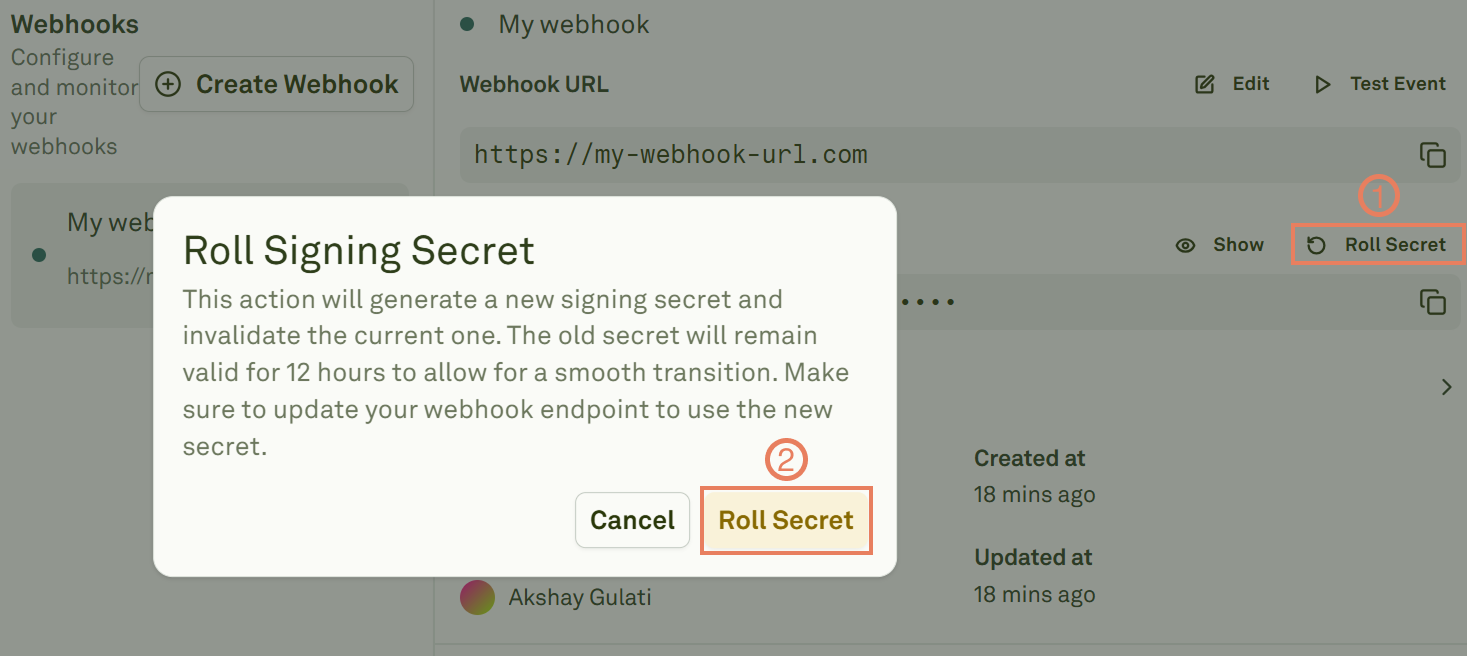
- Adaline creates new primary secret immediately.
- The previous secret is retained as a “rolled secret” and remains valid for 12 hours.
- During this time window,
X-Webhook-Signaturemay include multiple signatures so your server can accept either secret.
Troubleshooting
In case you need troubleshooting, consider the following:- Your endpoint returns a
400or401error: Confirm you parse the full raw request body before verification. - Signature mismatch: Check clock skew and ensure you use the same
{timestamp}.{payload}concatenation. - No header present: Ensure a signing secret is configured and the event includes a body.